依照慣例小聊一下 「要參加嗎?我要寫什麼當主題呢?大家都喜歡看什麼樣的內容?我寫的完嗎?三十天其實有點多,會不會沒內容?」 這大概就是我在開賽前的內心活動。 在想要不要開賽的時候一直在思考,思考自己在賽期的其他安排、思考自己是否有時間完成這樣的每日任務、思考自己有沒有足夠多的內容可以支撐三十天,總之我真的想了挺多的。後來因為牛肉湯的其他成員們(yunshiuan、owl_d、檸檬、白臉貓、Panda)也都決定開賽,那身為社長的我肯定也不能不出現吧,所以我們最後就組成了 6 人小隊,牛肉湯加油! 結果真的開始寫了之後,好不容易已經寫了好幾天,結果卻發生了一件超大的慘事。 我不小心把整個文章所在的資料夾刪掉了。== 明明記得自己都有做好備份,也明明記得自己都有 git push 但是卻居然直接消失!!十幾天之間寫的內容瞬間連灰都不剩,我甚至都開始懷疑自己是不是真的有寫過還是自己做了一個很長的夢。而且自己寫過的很多內容都已經忘記當初是如何編排進度,還有內容的詳細程度等等,所以當我現在開賽當天在寫這篇的時候,就是完全只能憑記憶與印象去拼湊內容。 「天將降大任於斯人也,必先苦其心志,勞其筋骨 ...
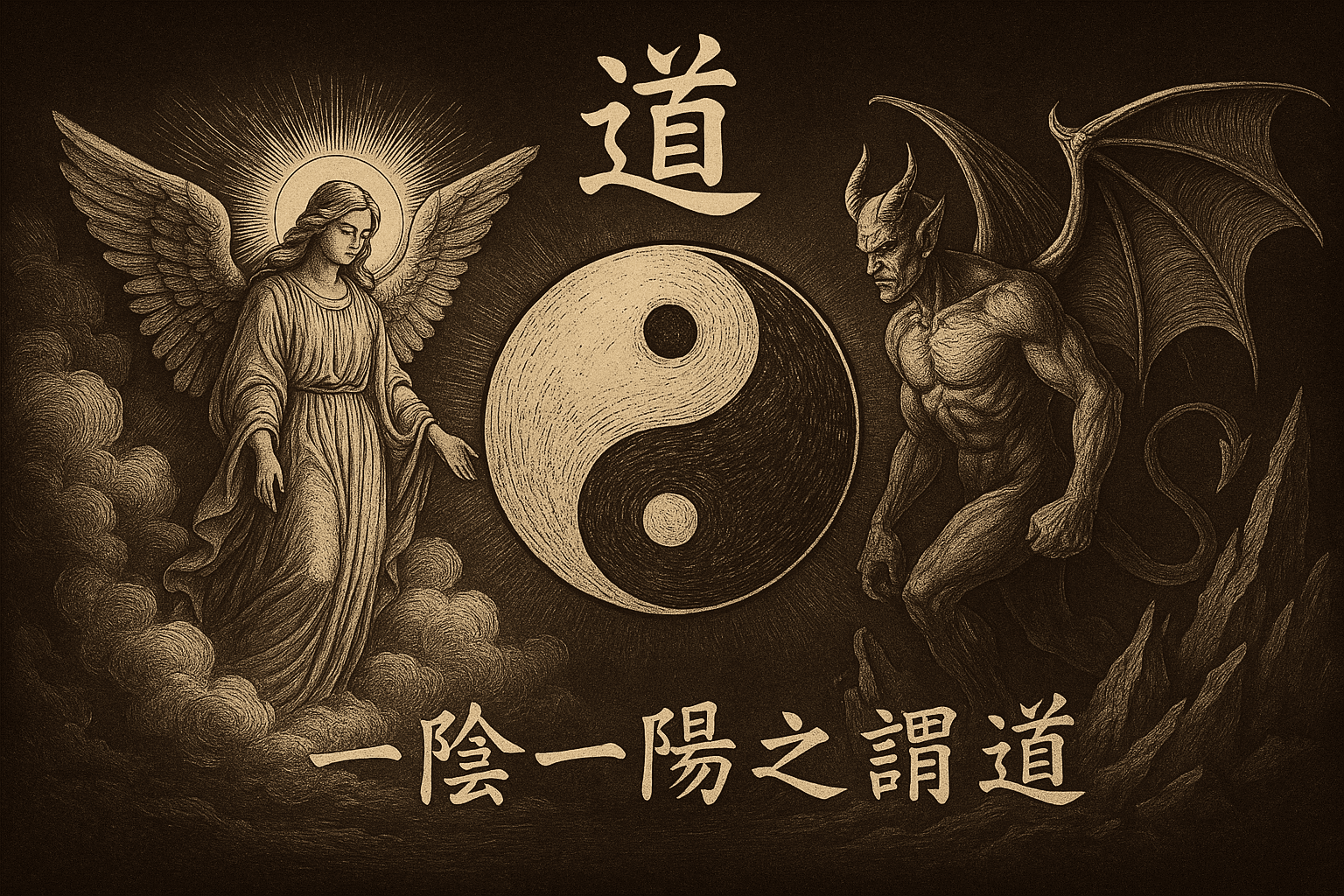
Prologue - What is Tao 「一陰一陽之謂道。」——《周易》 In this blog, I’ll introduce Tao, the malware uses Heaven’s Gate and Hell’s Gate techniques. I’ll try to explain the principles behind each of these distinct malware techniques and show how I design Tao in Zig programming language. By the way, this article is not my own research, it references plenty of other researchers’ findings. So it acts more like a note I took while learning from others’ research. If you got time, please take a look at those resear ...
Windows Data Types The Windows API has many datas types outside of the well-known ones (e.g. int, float). The data types are documented and can be viewed here. Some of the common data types are listed below: DWORD - A 32-bit unsigned integer, on both 32-bit and 64-bit systems, used to represent values from 0 up to (2^32 - 1). DWORD dwVariable = 42; size_t - Used to represent the size of an object. It’s a 32-bit unsigned integer on 32-bit systems representing values from 0 up to (2^32 - 1 ...
StudyNotes
UnreadHTB CBBH Experience Sharing Finally, I’ve got my CBBH certification from HackTheBox on last friday! This certification is totally underrated! It’s content is well-organized & comprehensive. I would say that this is really a good start if you’re interested in offensive web security. It’s a unforgettable experience, and here are some tips for those who also want to join the CBBH gang! 📚 Go through the content twice There’s really A LOT in the whole CBBH content, from different attack approach ...
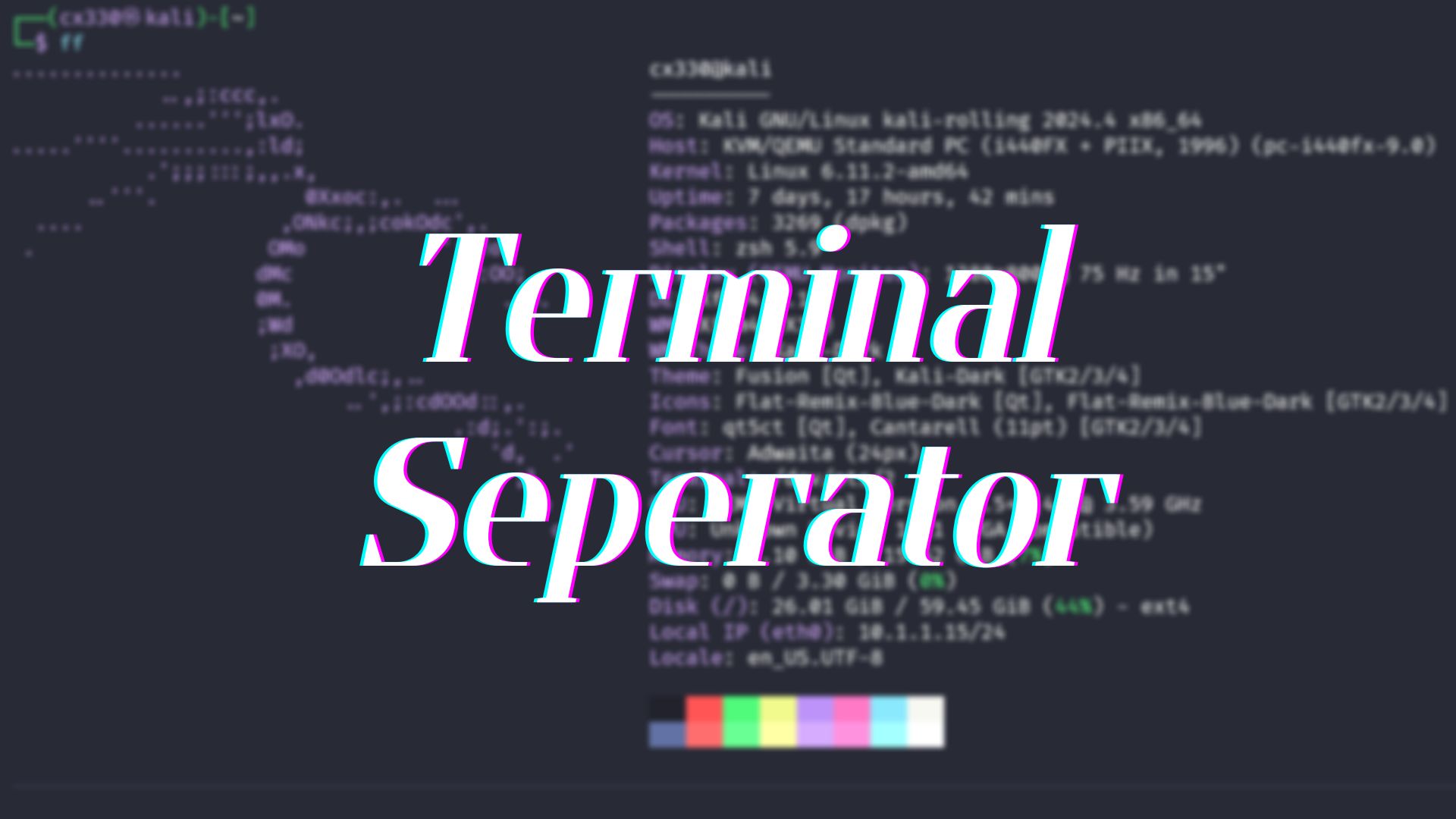
Why this? Why? Just since it makes my terminal looks prettier and easier to understand. It devides every command into a BLOCK so that I can easily get to the point. How it looks like? The gray line in the graph is how it looks like. You can change the color later in your setup. Setup function print_separator() { local cols=$(tput cols) local color="\033[38;2;68;71;90m" # RGB(68, 71, 90), you can change the color here local reset="\033[0m" printf "\n" printf ...
TryHackMe
Unread0x00 Challenge Info Obviously, it’s an LFI vuln. The web application can read the local file to response the different page. 0x01 Reconnaissance We can found that the file can be read by such as page=file:///etc/passwd. 0x02 Exploit Use the file:///flag.txt to read the flag.txt in the root path. 0x03 Pwned
Prologue This is the first time I have won a place in a CTF contest. Following are the score board and my score over time. Web Ave Mujica After some recons, I found the web server is built by gunicorn, and the web looks like having a directory traversal to LFI vulnerability. After I go do some research, I tried some LFI wordlist and finally got the flag by reading the /proc/self/environ. The PoC is as follows. curl 'http://172.31.3.2:168/image?name=../../../../proc/self/environ' --output flag. ...
Easy Crack Open IDA and find the check password function (you can use a string to find it). I will put the decompiled function below. int __cdecl sub_401080(HWND hDlg) { CHAR String[97]; // [esp+4h] [ebp-64h] BYREF __int16 v3; // [esp+65h] [ebp-3h] char v4; // [esp+67h] [ebp-1h] memset(String, 0, sizeof(String)); v3 = 0; v4 = 0; GetDlgItemTextA(hDlg, 1000, String, 100); if ( String[1] != 'a' || strncmp(&String[2], Str2, 2u) || strcmp(&String[4], aR3v ...




![[THM] Lo-Fi Writeup](https://raw.githubusercontent.com/CX330Blake/MyBlogPhotos/main/image/TryHackMe.jpg)
.jpg)





