[HTB] Behind the Scenes Writeup

[HTB] Behind the Scenes Writeup
CX3300x00 Challenge Info
After struggling to secure our secret strings for a long time, we finally figured out the solution to our problem: Make decompilation harder. It should now be impossible to figure out how our programs work!
0x01 Reconnaissance
First we can run the binary to see what’s going on.
┌──(kali㉿kali)-[~/CTF/rev_behindthescenes]
└─$ ./behindthescenes
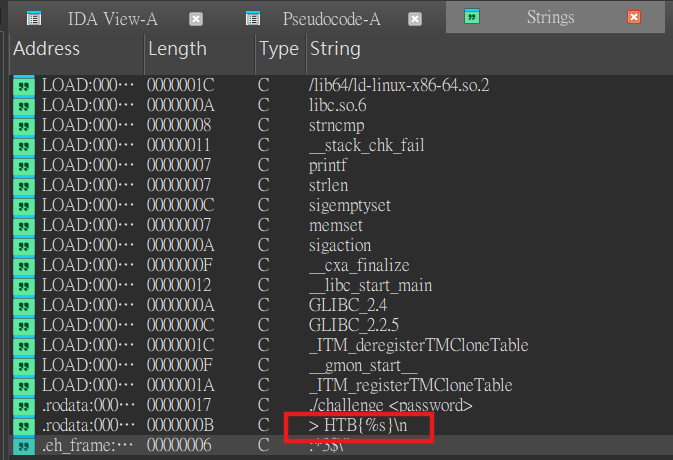
./challenge <password>It tell us we should put some password as the argument to execute this. Next step, I check the printable strings in the binary by using strings or the strings tab in IDA.
I found this is similar to the flag but we still don’t know the %s. So we can find some string that looks like the flag and fill it in.
0x02 Exploit
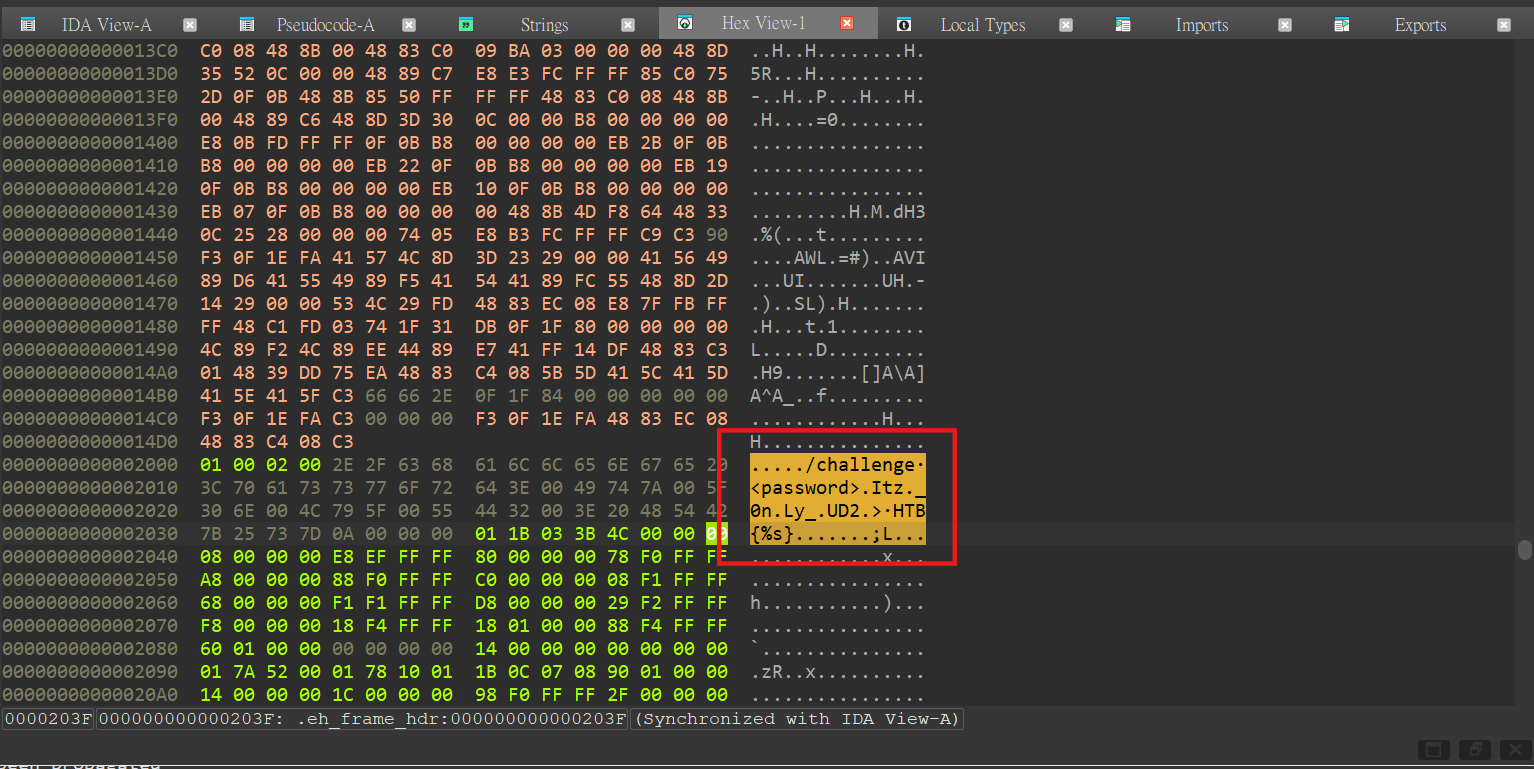
Finally I found it in the Hex View tab in IDA.
Then we run the binary with ./behindthescenes Itz_0nLy_UD2, it print out the flag!
0x03 Pwned
After I watch others writeups, I found that my solution may not be the official way, maybe it’s an unintended solution. It’s recommend to read the following writeup to learn more from this challenge.